

Svakom Siime Eye - we have withdrawn this vibrator from our range for safety reasons
Today I read a security advisory that provoked the reaction "Who the hell does that? A few minutes later, we withdrew a love toy from our range. The reason: a massive security breach.
The Svakom Siime Eye vibrator - pronounced "see me" - is no longer available from us. Perhaps a successor will find its place in our range, but only once its safety has convinced us. After all, safety is virtually non-existent with the Siime Eye. We know that we can no longer sell this product with a clear conscience. Which is something we want to avoid at all costs.
For it would appear that Svakom's Siime Eye is a failed product.

Let's look at this debacle in detail.
What is Svakom's Siime Eye?
Svakom is a company that creates love toys for women. The American company has gained notoriety for making products that produce pleasure in bed and are still quite aesthetically pleasing. The manufacturer plays on a short charging time and powerful motors.
The Siime Eye model is a trick in the Internet of Things. The Internet of Things is a generic term for anything intelligent. Devices that communicate with other devices are becoming ever more prevalent. As the sex toy industry is generally quite technologically advanced, the field of teledildonics has gradually become established. The term describes "sexual activity without physical presence". A bit like Sandra Bullock and Sylvester Stallone in "Demolition Man".
In contrast, the Siime Eye is far more presentable. The device not only has an internet connection to fulfil the features of teledildonics and a powerful motor, it also has a camera. Clearly, some people like this aspect and it needs to be taken into account. We all have a fetish, whether it's big or small, harmless or a little out of the ordinary. A short search on relevant video portals shows that the demand for videos taken from inside the human body is there.
A camera.
So we have a webcam in a device that is typically used in the bare region of a user's pelvis. So it would be a shame if these images were made public.
You can certainly see where I'm going with this.
The penetration test that brings it back to reality
In order for the Svakom Siime Eye to transfer images to the computer, it uses the WiFi standard. That is, the device becomes a WiFi access point. According to penetration testers at PenTestPartners, it makes sense for the device to use the WiFi standard because all standards like Bluetooth and others fail to retransmit a camera's signal without delay; which isn't very optimal, as romantic passions work best in real time.
Analysis of the source code shows that some of the device's data is hard-coded. This hard-coded programming is criticised by security researchers and, anyone with a mastery of the subject would advise against using hard code.
This data is critical:
IP: 192.168.1.1
Port: 80
SSID: Siime Eye
Username: admin
Password: [blank] (so empty)
If you are in the same home network as the Siime Eye, you can enter 192.168.1.1:80 in the browser of your choice, enter the username "admin" and leave the password field blank. Admittedly, during configuration, the manufacturer will tell you to change the password, but this is pointless if a user name and password are already specified in the source code. Because no one can change or influence them.
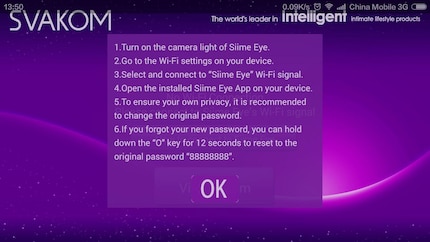
What's going on?
**The browser shows the video recording of the Siime Eye.**The web app that is trademarked for the Svakom Siime Eye looks like a standard camera app, like that of web portals with webcam control. Added to this are other functions such as "record video when motion is defined". In addition, parameters such as "skype_pw" are pre-recorded and enable a connection to the Internet telephony service Skype. This is not a security flaw, but a huge breach.
Detailed analysis of the code has shown that the code used for the Siime Eye was certainly written for drones. The names used in the code lead to a drone called Skyviper. PenTestPartners has made enquiries with the company and they were not aware that their code was being used for love toys.
The app that isn't safe either
The Siime Eye is usually controlled by an app for Google Android or Apple iOS. The access data is, again, obvious.
SSID: Siime Eye
Password: 88888888
This data must be entered when first connecting with the Siime Eye access point. Otherwise, the application cannot communicate with the vibrator. The app itself has only limited functionality. It can take photos and record videos. Videos can be played back.
Summary of the two weak points: anyone connected to the same network as the Siime Eye or in the vicinity of the toy's WiFi access point can access the video recordings.
.. great.
With a little more skill, the researchers at PenTestPartner managed to take full control (root access) of the device in the long term. In the world of information security, the Siime Eye will certainly go down in history as the device that turned the phrase "Root on vibrator" into reality.
So here's a word of advice: throw away your Siime Eye. We have other alternatives.
If you still want a camera for teledildonics, we've created the following bundle.
Journalist. Author. Hacker. A storyteller searching for boundaries, secrets and taboos – putting the world to paper. Not because I can but because I can’t not.



